“We are living in the middle of a cyber war,” said Christophe LeSieur, Global Practice Lead of Governance, Risk & Compliance (GRC) at CSC. He was the first of two presenters at a webinar on cybersecurity sponsored by the Global Association of Risk Professionals held on December 16, 2014.
He described “the new normal” as “an environment of unprecedented tension” whose mega-trends are: social media, information technology (IT) and internet everywhere, proliferating platforms (mobile, bring your own device[BYOD]), and a huge quantity of data.
The world is becoming ever more different, and the number of attacks is growing. Just this week, the news broke about the North Korea cyberattack on Sony. In the financial sector, in 2013, TD Bank was the victim of a cyber attack. In 2012, Iranian hackers attacked Bank of America, JPMorgan Chase, and Citigroup. LeSieur referred to several news stories in 2014. Cybersecurity is threatened by a range of persons: from “creative and bored students” up to “military type organizations,” he said.
The infrastructure is growing more intricate, and that makes control more difficult. Regulatory requirements are also increasing in number and complexity.
“Cybersecurity is a priority” in best practice institutions. “It’s not just installing a piece of software,” LeSieur said. “You must look at the whole IT environment.” That includes how to link cyber risk with existing risk management and governance processes.
Risks constantly change, in scope, velocity, complexity, and impact. “Cyber risks need to be quantified… at the board level,” said LeSieur. Cyber risk should be embedded in operational risk and in this manner brought into the arena of capital management. “Managing your security risk is not just something on the lower operations level,” he emphasized.
In a post-webinar aside, LeSieur noted these types of risks are “captured” and possibly mitigated on the operational / IT level, but are not adequately reported into the management information systems . Also, the risks are very often not reported correctly in the corporate enterprise resource planning. For instance, a pure financial loss /damage figure might occur in systems, applications, and products (in data processing), but the cause or origin of the incident / loss would not be adequately reported.
LeSieur summarized the most “top-of-mind challenges” in cyber security and proven approaches to overcome these challenges.
One of these methodologies is the so called cybersecurity “kill chain”–actually derived from a military approach (“watch chain” and “kill chain”)–to the cyber war and most notably presented 2011 in a influential paper on computer network defense by Hutchins, Cloppert, Amin at Lockheed Martin–to which LeSieur referred. The article states: “the intrusion kill chain provides a structure to analyze intrusions, extract indicators and drive defensive courses of actions.”
In common terms, LeSieur explained, “the kill chain is the battle plan for your cyber war.” He touched briefly on the seven phases of the plan and gave examples for each: reconnaissance, weaponization, delivery, exploitation, installation, command & control (C2), and actions of objectives.
For each phase, LeSieur posed the question: “how well prepared is your organization?” Can it detect, deny, disrupt, degrade, deceive, and contain? He showed an example of an organizational assessment for cyber risk in the form of a familiar “heat-map” where green indicates standards are being met or exceeded, red indicates a problem area, and yellow is in-between. (The accompanying figure shows a portion of the example heat-map.)
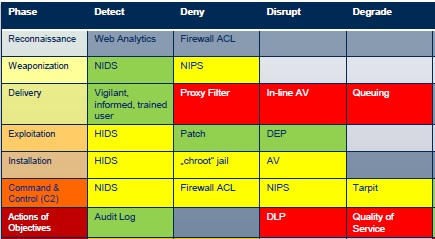
Adapted from materials from Intelligence and National Security Alliance (INSA) as well as National Institute of Standards and Technology (NIST), RAND, and Verizon.
For example, the use of malware to create an open door to an organization’s information, can be detected through a good network intrusion detection system (NIDS) that merits a green indicator, but the threat may be denied through a network intrusion prevention system (NIPS) that needs improvement, and therefore merits a yellow on the heat-map. The organization should work to correct all areas of weakness in its heat-map.
Above all, LeSieur emphasized the need to establish a continuous monitoring cycle. Cybersecurity is fast moving. “Your risk situation is continually moving, just like your environment.” ª
Click here to view the webinar presentation on cybersecurity. Christophe LeSieur spoke in two sections, covering slides 5 to 14, and slides 25 to 31.
The figure is adapted from materials from Intelligence and National Security Alliance (INSA) as well as National Institute of Standards and Technology (NIST), RAND, and Verizon.
Click here to view a report of the second presentation, Yo Delmar.